We’ve had a number of calls from GoAnywhere users recently, reporting email alerts for expiring certificates. These are certificates that come with a default GoAnywhere installation.
These alerts can be worrying, but in the majority of cases they can be safely ignored.
A number of root CA certificates are always delivered with new GoAnywhere installs. Theoretically these simplify things for administrators so they don’t have to organise a trusted root certificate to support their certificate chains. Let’s take a moment to look at what these certificates are used for:
Case 1 – Listeners
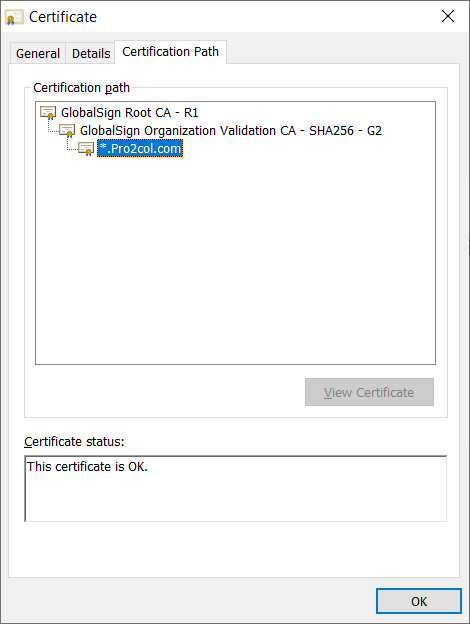
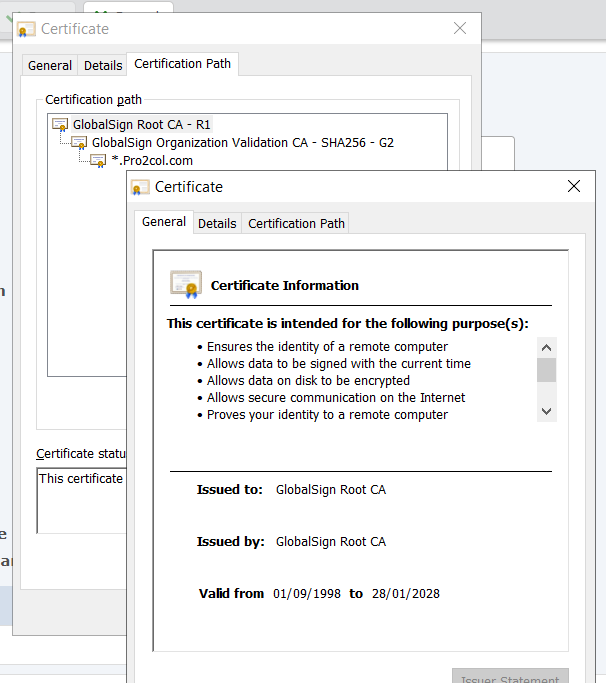
Each of your SSL-enabled listeners will have a corresponding certificate (normally the same one across all listeners). The servers in use by Pro2col for example, use a wildcard certificate to protect HTTPS and FTPS connections. The best way to see this is by checking the padlock in the browser. If you move to the certification path, you can see that the root CA (for us) is GlobalSign.
I can cross-reference this to my Key Management System, which I reach from the Encryption menu. Here I can see the root CA I have stored to match this certificate:
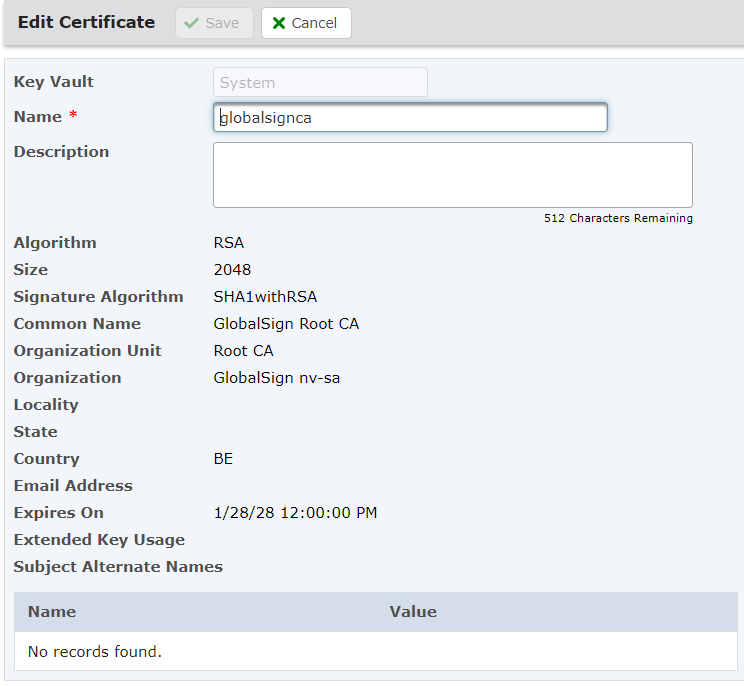
By checking back on the certificate displayed in the browser, I can see a clear match on dates.
Ordinarily you will rarely need more than one root CA certificate to protect your listeners, or two at most (if you periodically change CA).
Case 2 – Trusting other peoples certificates
The other reason I may need to use these Root CA certificates is to establish trust with public certificates that are presented to me – most commonly for HTTPS, FTPS or AS2. Remember that at the top of every certificate chain there should be a trusted root CA certificate. We can use root CA certificates in our key store to validate that the trust chain in a public certificate presented to us is authentic.
Certificate Expiry
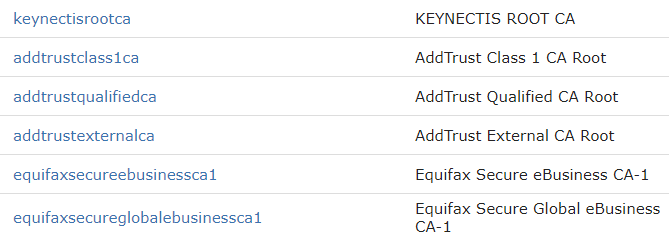
Up-to-date certificates are included in new installs but NOT in the case of upgrades. That’s because you may already have replaced a certificate and do not want it to be overwritten. So inevitably, these root CA certificates will expire. For example, on the Pro2col GoAnywhere server the following root CA certificates will expire in May and June 2020:
There is, however, no easy way to determine if these root CA certificates are in use anywhere in the system. The two ways that you can check are (and neither of these methods is great!) as follows:
- Check your non-root certificates to see if any of them use these root certificates
- Export the certificate to your computer, then delete it from the system to see if something breaks.
In the unlikely event that you DO need the certificate, please contact us and we can assist you with the process of importing new certificates
Finally, it’s worth pointing out that these email notifications of expiring certificates are optional. I if you are not receiving any alerts but have expiring certificates, you can check the notification settings under System – System Alerts.
